1. Background & Purpose
- 1.1 The goals of this policy and any supporting policies is to ensure that our digital information is:
-
- 1.1.1 Available: assurance that authorized individuals have both timely and reliable access to data and other resources when needed.
-
- 1.1.2 Accurate: assurance that information is not intentionally or accidentally modified in such a way as to call into question its reliability.
-
- 1.1.3 Confidential: assurance that sensitive information is not intentionally or accidentally disclosed to unauthorized individuals.
- 1.2 This policy and any supporting policies and procedures constitute Mount Allison’s Information Security Program to ensure all necessary measures are in place to achieve the goals in paragraph 1.1.
- 1.3 This policy is intended to outline the responsibilities of those who have access to University electronic information and the services, devices and systems that store or transmit this information.
- 1.4 Any supporting policies and procedures are to provide further clarity and detail on various aspects of information security required under this policy.
- 1.5 Definitions of Roles and Responsibilities are described in Appendix 1.
- 1.6 The Vice-President, Finance and Administration may adopt standards and procedures consistent with this policy for the University while departments may adopt implementation procedures that reflect departmental circumstances, provided they too are consistent with this policy.
- 1.7 Nothing in this policy shall derogate from any right any staff or faculty member has under a collective agreement or any responsibility the University has under law or regulations.
- 1.8 The university is committed to the principle of academic freedom. This policy should be interpreted in that context.
2. General
- 2.1 All Users of Mount Allison University Electronic Information and Systems are responsible for using them responsibly and for maintaining their security.
- 2.2 Users who breach this policy may be subject to disciplinary actions subject to any applicable collective agreement. In addition to any other sanctions that the University may impose in the event of a violation, the Director of Information Technology, or their designate, may restrict or withdraw access to Mount Allison University Electronic Information and Systems, including computing privileges and network access.
- 2.3 The Director of Information Technology or delegate shall perform a coordinating role in the implementation, administration, and support of this policy by:
-
- 2.3.1 providing guidance on compliance with the policy;
-
- 2.3.2 providing an ongoing security awareness program; and
-
- 2.3.3 assisting, where appropriate, in the investigation of breaches and potential breaches of the policy.
- 2.4 If a User becomes aware that Electronic Information and Systems are not being used appropriately, the User should bring this to the attention of the relevant administrative department head or to the Director of Information Technology so that appropriate action can be taken to address the situation.
- 2.5 This policy applies to all Mount Allison University Electronic Information, except as otherwise provided by paragraph 2.6.
- 2.6 Where a Mount Allison University System is not intended to be used for University Business, the Director of Information Technology must, in consultation with the Vice President Finance and Administration approve separate terms of use that govern the use of such system. Upon such approval, this policy will not apply to such system.
3. Definitions
- 3.1 “Academic Freedom” is defined in the collective agreements with Mount Allison Faculty Association.
- 3.2 “Information Security Program” includes this policy and all supporting policies and procedures describing the steps required to ensure the safety and security of Mount Allison electronic information and systems.
- 3.3 “Mount Allison University Electronic Information” is electronic data needed and created to conduct University Business.
- 3.4 “Mount Allison University Electronic Information and Systems” includes Mount Allison University Electronic Information and Mount Allison University Systems both on campus and hosted elsewhere off campus.
- 3.5 “Mount Allison University Systems” are services, devices, and facilities that are owned, leased or provided to the University, and that are used to store, process or transmit electronic information. These include, but are not limited to:
-
- 3.5.1 computers and computer facilities;
-
- 3.5.2 computing hardware and equipment;
-
- 3.5.3 mobile computing devices such as laptop computers, smartphones, and tablet computers;
-
- 3.5.4 electronic storage media such as CDs, USB memory sticks, and portable hard drives;
-
- 3.5.5 communications gateways and networks;
-
- 3.5.6 email systems;
-
- 3.5.7 telephone and other voice systems; and
-
- 3.5.8 software.
- 3.6 “University Business” means activities in support of the administrative, academic, and research mandates of the University.
- 3.7 “Users” are faculty, staff, students, and any other individuals who use Mount Allison University Electronic Information and Systems.
4. Use of Mount Allison University Electronic Information and Systems
- 4.1 Mount Allison University Electronic Information and Systems may only be used in a manner that is consistent with:
-
- 4.1.1 applicable laws, and;
-
- 4.1.2 this and other applicable policies, and;
-
- 4.1.3 collective agreements with faculty and staff; and
-
- 4.1.4 the terms of employment applicable to non-unionized staff.
- 4.2 Incidental personal use of Mount Allison University Electronic Information and Systems is acceptable provided that such use does not interfere with the User’s job performance and is not a prohibited use as per paragraph 4.3 of this policy.
- 4.3 Prohibited uses of Mount Allison University Electronic Information and Systems are any uses that disrupt or interfere with the use of the resources for their intended purpose.
The following are examples of prohibited uses:
-
- 4.3.1 breaching applicable laws or university policies;
-
- 4.3.2 sending threatening, harassing or discriminatory messages;
-
- 4.3.3 misrepresenting the User’s identity as sender of messages;
-
- 4.3.4 intercepting or examining the content of messages, files, or communications without authorization;
-
- 4.3.5 infringing upon the copyright of computer programs, data compilations and all other works (literary, dramatic, artistic or musical);
-
- 4.3.6 infringing upon the legal protection provided by trademark law and the common law for names, marks, logos, and other representations that serve to distinguish the goods or services of one person from another;
-
- 4.3.7 making unauthorized copies of proprietary software, or offering unauthorized copies of proprietary software to others;
-
- 4.3.8 failing to maintain the confidentiality of passwords, access codes or identification numbers used to access Mount Allison University Electronic Information and Systems;
-
- 4.3.9 seeking information on passwords or information belonging to another User without authorization;
-
- 4.3.10 accessing or examining other accounts, files, programs, communications or information without authorization;
-
- 4.3.11 destroying, altering, dismantling, disfiguring or disabling Mount Allison University Electronic Information and Systems without authorization;
-
- 4.3.12 damaging or altering the hardware or physical components of Mount Allison University Systems without authorization;
-
- 4.3.13 attempting to circumvent security controls on Mount Allison University Electronic Information and Systems without authorization;
-
- 4.3.14 knowingly introducing malware; and
-
- 4.3.15 engaging in any uses that result in the loss of another User’s information without authorization.
- 4.4 Nothing in paragraph 4.3 shall be construed as preventing or restricting duly authorized system administrators or other technical personnel from carrying out their duties.
5. Security of Mount Allison University Electronic Information and Systems
- 5.1 All Users must comply with the Information Security Standards established under this policy regarding the security of Mount Allison University Electronic Information and Information Systems.
- 5.2 The Vice President Finance and Administration is responsible for:
-
- 5.2.1 developing and issuing any supporting Information Security Policies and Procedures, which must be consistent with this policy;
-
- 5.2.2 publishing the Information Security Policies and Procedures on the Mount Allison University web site for access by all Users; and
-
- 5.2.3 reviewing the Information Security Policies and Procedures on a bi-annual basis or at such other interval as the Vice President Finance and Administration determines.
- 5.3 Individuals who wish to deviate from the Information Security Policies and Procedures are required to request the authorization of the Vice President Finance and Administration before proceeding.
- 5.4 Where the Information Security Policies and Procedures do not address the reasonable requirements of an individual’s use of and access to Mount Allison University Electronic Information or Systems, the Vice President Finance and Administration may authorize a variance or update the Information Security Policies and Procedures as appropriate.
6. Use of Non-University Systems for University Business
- 6.1 To maintain the security of Mount Allison University Electronic Information, Users intending to conduct University Business using systems other than Mount Allison University provided systems must do so in accordance with the Information Security Standards.
7. Privacy of Users
- 7.1 Since paragraph 4.2 of this policy authorizes the incidental personal use of Mount Allison University Electronic Information and Systems, the University recognizes that these resources may contain records relating to this personal use, e.g. personal emails, documents, voicemails, text messages, and records of internet and social media use (the “Personal Use Records”).
- 7.2 While the University takes reasonable measures to back up information and protect it from loss, the University cannot guarantee that Personal Use Records will be retained in the Mount Allison University Systems or remain confidential. To protect their Personal Use Records from inadvertent access, disclosure or destruction, Users are encouraged to store them separately from Mount Allison University Electronic Information and back them up on a regular basis. Personal Use Records may be subject to Requests under the New Brunswick Request to Information and Protection of Privacy Act (RTIPPA).
- 7.3 Users should understand that the University routinely monitors network transmission patterns such as source/destination, address/port, flags, packet size, packet rate, and other indicia of traffic on Mount Allison University Systems. University system administrators and other technical personnel also perform routine maintenance of Mount Allison University Systems. This routine monitoring and maintenance may unintentionally reveal Personal Use Records.
- 7.4 The University will not intentionally access, use or disclose Personal Use Records unless it has the consent of the User, or:
-
- 7.4.1 securing the User’s consent would compromise (a) the health or safety of an individual or a group of people, (b) the availability or accuracy of the information, or (c) an investigation or a proceeding related to a breach of law or policy or the employment of the User;
-
- 7.4.2 the University is legally authorized to do so.
8. Administrative Responsibilities
- 8.1 Vice Presidents, Deans and Directors are responsible for establishing and maintaining Mount Allison University Electronic Information and Information Systems within their areas of responsibility. These responsibilities include:
-
- 8.1.1 ensuring that Mount Allison University Electronic Information and Information Systems are secured with adequate controls, with particular care concerning User identification and validation measures;
-
- 8.1.2 ensuring, as appropriate or required, that Mount Allison University Electronic Information within their area of responsibility is maintained, transmitted, and stored in a secure and consistent manner that adheres to all relevant University policies and standards;
-
- 8.1.3 authorizing access for individuals to Mount Allison University Electronic Information and Information Systems within their area of responsibility;
-
- 8.1.4 renewing, retiring, and revoking User authorizations within their area of responsibility;
-
- 8.1.5 ensuring that a contingency plan, including appropriate data back-up systems and recovery systems, is being used within their department;
-
- 8.1.6 ensuring that breaches and potential breaches of this policy occurring within their department are resolved and/or referred to the Director of Information Technology, as appropriate, and that where they are so referred, continuing to assist in the investigation, preserving evidence where required;
-
- 8.1.7 ensuring that technical staff within their department are aware of and adhere to this policy, and that they support University standards in the design, installation, maintenance, training, and use of Mount Allison University Electronic Information and Systems;
-
- 8.1.8 working with Mount Allison University Computing Services to make training and other information and resources necessary to support this policy available to Users in their department; and
-
- 8.1.9 taking immediate and appropriate action when they become aware of violations of this policy or its procedures.
Appendix 1
Roles and Responsibilities
The Table below describes the roles and related responsibilities of the various functions required for the effective operation of Mount Allison University's Use and Security of Electronic Information and Systems Policy and supporting Policies and Procedures.
|
Role |
Responsibilities |
Delegation of Responsibilities |
|
VP Finance & Administration |
Has overall responsibility for the Information Security Policies, Standards, and Procedures as set out in the Use and Security of Electronic Information and Systems Policy, section 8. |
May delegate responsibilities to Director of Information Technology or appropriate designate. |
|
VPs, Deans, Directors |
Responsible and accountable for establishing and maintaining Mount Allison University Electronic Information and Information Systems within their areas of responsibility, as set out in Use and Security of Electronic Information and Systems Policy, section 8. |
May delegate responsibilities to Information Stewards/Owners, University IT Support Staff, and other individuals where appropriate. |
|
Information Steward / Owner |
Appointed by applicable Vice President, Dean or Director to be responsible for a specified Mount Allison University System, database or collection of Mount Allison University electronic information. Determines:
|
n/a |
|
Computing Services Staff |
Assists the VPs, Deans and Directors or delegate to implement Information Security Policies |
n/a |
|
User |
Someone who uses or accesses Mount Allison University Electronic Information and Systems. Must comply with all Information Security policies relevant for Users. |
n/a |
Glossary of Terms
Confidential Information is Mount Allison University Electronic Information that must be protected by law or regulation from unauthorized access, use or destruction, e.g. Personal Information and Payment Card Industry (PCI) Information. See also Sensitive Information and Public Information.
Payment Card Industry (PCI) Information includes credit card numbers, cardholder names, expiry dates, PINs, and service codes.
Personal Information is as defined by the Right to Information and Protection of Privacy Act which states: “identifying information” means information that identifies an individual or which it is reasonably foreseeable in the circumstances could be utilized, either alone or with other information, to identify an individual. This includes recorded information about an identifiable individual, with the exception of the names and business contact information of employees, volunteers and service providers. Examples of Personal Information include student names, grades, personal email addresses, home addresses, health information, donor names, prospective employee names, and personal banking information.
Public Information is Mount Allison University Electronic Information that may be freely released to the public. Examples of Public Information include the names and titles of Mount Allison University employees. See also Confidential Information and Sensitive Information.
Sensitive Information is Mount Allison University Electronic Information that is not protected by law or industry regulation from unauthorized access, use or destruction, but that nevertheless should be protected because releasing it could cause harm to Mount Allison University or others. Examples of Sensitive Information include plans of Mount Allison University facilities, locations of vulnerable research units, financial data, server/network configurations, and copyrighted material. See also Confidential Information and Public Information.
Security and Classification of Mount Allison Electronic Information Procedure
1. Introduction
Mount Allison Electronic Information used by Users, has varying degrees of sensitivity which have corresponding levels of risk and protection requirements; therefore, it is necessary to classify this information to ensure it is given the appropriate level of care and custody.
This explains how Mount Allison Electronic Information is classified using Mount Allison’s three-level Information Security Classification Model.
This has been issued under the authority of the Use and Security of Mount Allison Electronic Information and Systems Policy. Questions may be referred to helpdesk@mta.ca
2. Information Security Classification Model
Mount Allison Electronic Information is classified as follows:
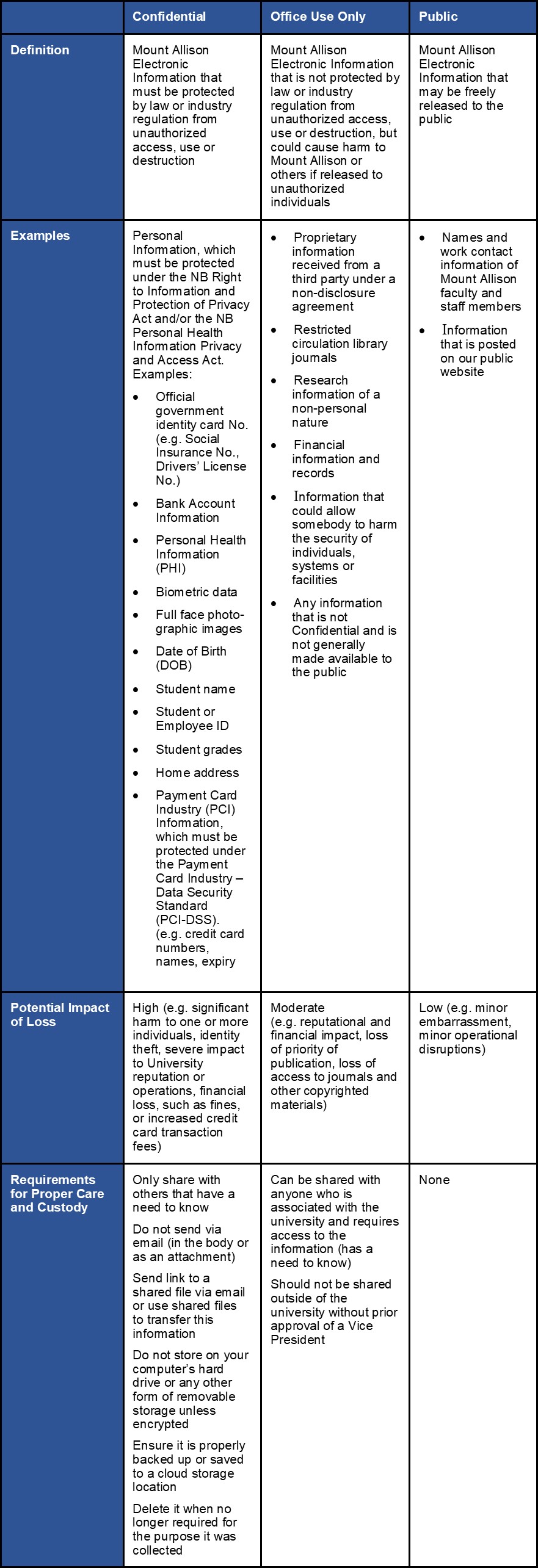
3. Responsibility for Classifying and Caring for Information
The Data Steward/Owner is responsible for determining the information security classification based on the definitions and examples in the table above. Based on other relevant factors, information may be classified at a higher level than indicated above, but not at a lower level.
The Vice President’s, Deans and Directors are responsible for knowing the types of Mount Allison Electronic Information under their control, its information security classification and where it is stored. This responsibility may be delegated to the Information Steward/Owner.
All users are required to provide the corresponding levels of care and custody of University information while in their possession and control.
Related Documents
6300 – Archives Policy
Electronic Data Retention and Destruction Procedure
1. Background & Purpose
1.1 The University has electronic information, including records which are defined as personal information under the Right to Information and Protection of Privacy Act (“RTIPPA”) and has obligations regarding the safe keeping of this information.
1.2 Records can be categorized as low, medium, or high risk where risk is measured based on the impact to the University or a 3rd party if the record was to be inappropriately accessed.
1.3 This document sets guidelines for Users on the retention, destruction and/or sanitization of Mount Allison Electronic Information (data destruction).
1.4 The Vice President Finance and Administration has issued this document under the authority of the Use and Security of Electronic Information and Systems Policy. Questions about this standard may be referred to helpdesk@mta.ca
2. Responsibilities of Users
2.1 Users should only retain information as long as required for its intended use.
2.2 Prior to deleting electronic information users must take into consideration the requirements of the Archives Policy 6300. Consult with the University Archivist if in doubt.
2.3 Users are responsible for ensuring that Mount Allison Electronic Information is always removed from a Device (Desktop, laptop, tablet, smart phone) before the device is transferred to another individual, sold, or discarded. The information needs to be removed even if it does not appear to be Medium, or High Risk. Users should contact the Helpdesk (helpdesk@mta.ca) if they require data destruction assistance.
3. Responsibilities of Service Providers
3.1 Where a third party Service Provider has received copies of Mount Allison Electronic Information for the purpose of Mount Allison work, the Service Provider must destroy all of the information in its possession within seven days of the completion of the project or termination of the agreement, whichever first occurs, using destruction methods compliant with this policy and give the Mount Allison contract owner a signed confirmation of destruction.
3.2 Where data destruction is not feasible, The Mount Allison contract owner may consult with Computing Services to determine appropriate alternate controls.
4. Approved Destruction Methods
4.1 Any of the following are approved methods of data destruction:
- 4.1.1 using a software utility, such as "Secure Erase", that erases, overwrites or encrypts the data;
- 4.1.2 magnetically erasing (degaussing) the data;
- 4.1.3 formatting a Device after encrypting it; or
- 4.1.4 using a machine that physically deforms or destroys the Device to prevent the data from being recovered.
4.2 Using the “Empty Recycle Bin/Trash”, “Delete”, “Remove”, and “Format” operating system commands do not destroy data and therefore are not acceptable methods for preparing media for transfer or disposal.
4.3 Data destruction methods must comply with the minimum standards set out in the IT Media Sanitization (ITSP.40.006 v2) publication issued by the Government of Canada. https://www.cyber.gc.ca/en/guidance/it-media-sanitization-itsp40006
4.4 Wherever encryption is used before formatting a device, it must be AES-128/256 bit encryption with strong passwords or passphrase. See Password Policy and Procedures - 7002
4.5 Questions about whether a mode of destruction is an approved method can be directed to helpdesk@mta.ca
5. Special Cases
5.1 To reuse flash memory devices (e.g. SD memory cards, USB drives) containing Mount Allison Electronic Information, the User can encrypt the whole device. After encryption, the User can format the device and reuse it safely.
5.2 Smartphones must have all data removed (factory reset) prior to being transferred to another person or being turned in for recycling; note that some smartphones have removable memory cards that need to be treated the same as flash memory devices and securely sanitized separate from a phone factory reset. Users can contact the CSD Helpdesk if they are uncertain of how to perform a factory reset.
5.3 Other imaging devices with a hard drive (e.g. photocopiers, printers, fax machines, etc.) are also subject to the data destruction requirements; additionally, where possible, these devices should have image overwriting enabled. This is a function where scanned or electronic images of a document are immediately overwritten using a data destruction technique. This function is known by various names, e.g. “Immediate Image Overwrite” (Xerox), “Hard Disk Drive Erase Feature” (Canon), “Hard Disk Overwrite Feature” (HP)
Related Documents Password Policy and Procedures - 7002

